
Access Control Systems
Imagine a school where unauthorized visitors are deterred, student safety is prioritized, and access is granted only to those who belong. ICU Technologies' access control systems make this vision a reality.
Safeguarding Your School
Who, What, Where, When: Maintaining Control Over School Access
Access control systems play a vital role in ensuring the safety of students, faculty, and staff on campus. Leading-edge systems regulate who enters your school building, specific areas within the school, and at what times. By granting access only to authorized individuals, control systems deter unauthorized visitors, streamline entry procedures, and provide valuable data for security purposes.
Enhanced Security with Access Control Features
Advanced access control systems offer a powerful toolbox for safeguarding your school. ICU Technologies' access control solutions do more than just restrict entry from unwanted visitors. Our comprehensive suite of features is designed to empower informed decision-making and bolster campus security, allowing you to create a more secure learning environment for your campus.

Role-Based Access Control: Grant different access levels to staff, students, parents, and visitors, ensuring only authorized individuals can enter specific areas.
Real-Time Monitoring & Reporting: Track who enters and exits your school in real-time, and generate detailed reports for security audits and investigations.
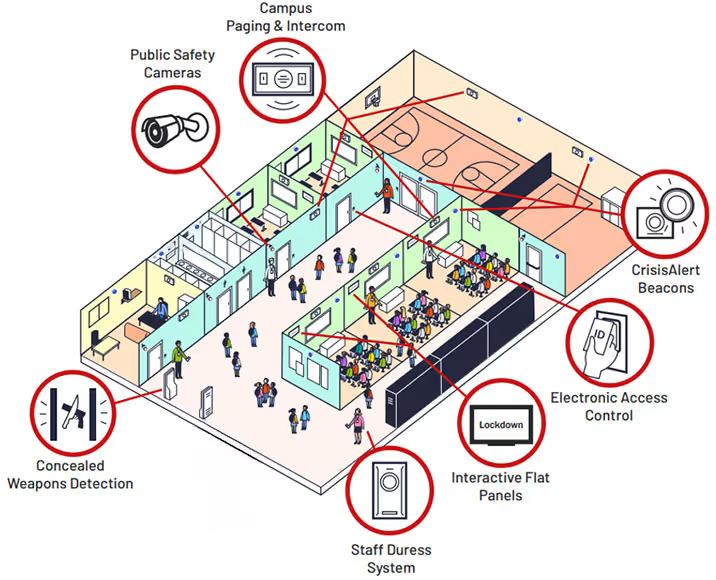
Integration with Other Security Systems: Integrate your access control system with cameras, alarms, and other security measures for a unified approach to campus safety.
Enhanced Security During Emergencies: Lockdown features can be implemented instantly during emergencies, securing the school and protecting occupants.
Streamlined Entry & Reduced Wait Times: Eliminate the need for physical keys and expedite entry procedures with user-friendly access credentials like key cards or mobile phone apps.
The ICU Technologies Difference
A Multi-Layered Approach for More Secure Schools
At ICU Technologies, we understand that a single point of entry control isn't enough for optimal school safety. That's why we utilize a proven, multi-layered approach when designing access control systems. Our approach creates a more secure environment that deters unauthorized access and provides multiple lines of defense. By partnering with ICU Technologies, your school will gain a secure, efficient, and future-proof access control system that’s designed to meet the unique needs of your learning environment.
Collaborative Needs Assessment
We work closely to identify vulnerable areas, access requirements for different user groups, and integration needs with existing security infrastructure.
Strategic System Design
Our security specialists design a system that considers traffic flow, access levels, and potential security risks. This may involve layered access points, integration with video surveillance, and lockdown capabilities.
Seamless System Integration
We ensure your new access control system integrates smoothly with existing security measures, creating a unified security network.
Ongoing Support & Training
Comprehensive training for your staff on operating the system allows us to maximize the system’s functionality.
We’re Focused On Your Objectives
When it comes to safeguarding your school, ICU Technologies offers a unique blend of expertise and advanced technology. We don't just sell products – we deliver comprehensive security plans with a systematic approach that includes a thorough needs assessment, strategic system design, and seamless integration to ensure our access control system meets your evolving security needs. A symphony of security seamlessly integrates access control with other security measures to deliver a comprehensive and effective solution for your school. At ICU Technologies, we ensure future-proof security solutions.

Build a Safer Campus. Contact Our ICU Team
Learn More About Our Campus Access Control Systems
Contact ICU Technologies to explore how our multi-layered approach to school security helps districts identify and achieve their safety objectives. As a trusted security partner focused exclusively on K-12, we have the expertise to recommend the correct security technology strategies that best protect schools, as well as provide the expert access control installation services you expect.
CALL US: (530) 488.7200
Contact Our Team