
K-12 Security Solutions
Tailored Security Strategies for Schools
ICU Technologies has a deep understanding of K-12 safety requirements and guidelines, taking a multi-layered approach to school security.
Protecting your students, faculty, and staff is our top priority. We offer a comprehensive range of security solutions for K-12 institutions. From access control systems for schools that manage entry and deter unauthorized visitors, to advanced video surveillance for complete peace of mind, we can help you create a layered security approach to safeguard your school. Our solutions are scalable to fit the needs of any size school district.
 link is following to blog post
link is following to blog post
Bulletproof Glass Laminate
Discreet protection for schools. Bulletproof glass laminate can be customized to meet the specific needs of any campus.
Read More link is following to blog post
link is following to blog post
Weapons Detection Solutions
Frictionless AI-powered weapons detection systems are designed to detect threat objects with low false alarm rates.
Read More link is following to blog post
link is following to blog post
Security Cameras
Monitor every corner. Secure your school with advanced video surveillance systems.
Read More link is following to blog post
link is following to blog post
Access Control Systems
Safeguard your school. Access control systems manage entry and keep unauthorized visitors out.
Read More link is following to blog post
link is following to blog post
Personal Duress & Panic Alert
Wearable panic buttons can be clipped to a teacher's clothing and activated with a single click.
Read More link is following to blog post
link is following to blog post
Paging & Intercom Solutions
Clear communication. Efficient announcements. Paging and intercom systems designed for your campus.
Read MoreThe ICU Technologies Difference: A Layered Approach to Campus Security
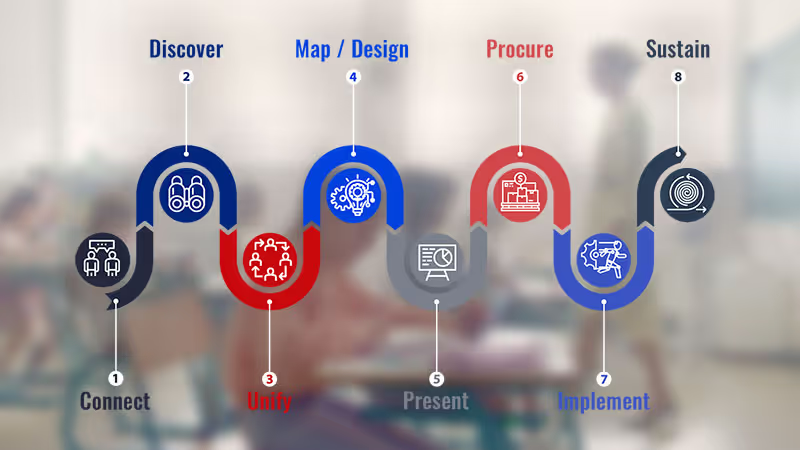
ICU Technologies goes beyond single-point solutions. Using our Proven Process, we design multi-layer campus safety strategies for schools that DEMAND MORE.
At ICU Technologies, we understand that true campus safety isn't achieved with a single security measure. Our Proven Process utilizes a layered approach, meticulously integrating multiple security technologies to create a comprehensive shield for your community. We’re committed to providing more than just products – offering a true partnership and working alongside district stakeholders to identify vulnerabilities, design customized security plans, and implement the right solutions to foster safe and secure learning environments.
Threat Prevention
Fast, Touchless Threat Detection Allows for Effective, Yet Unobtrusive, Entry Experiences
ICU’s next-generation threat prevention solutions are comprehensive and provide options for any of your school’s prevention program needs. Our multi-layered approach includes ballistic laminate, perimeter threat detection, touchless screening, and mobile duress and panic alerts.
Theft Prevention
Theft Deterrence & Asset Protection: Safeguarding Your School
Protecting your school's property shouldn't be an afterthought. ICU Technologies offers a comprehensive suite of theft prevention solutions designed to deter theft, secure belongings, and ensure your students remain focused on learning, not loss.
Event Detection
Proactive Response: Event Detection Systems for Schools
Don't wait for incidents to occur. ICU Technologies offers advanced event detection systems that analyze multiple data points to identify potential threats and suspicious activity in real-time. This proactive approach empowers stakeholders to intervene before situations escalate, fostering a safer and more secure learning environment for your entire school community.
Situational Awareness
Heightened Awareness, Enhanced Safety: Situational Awareness Solutions for Schools
ICU Technologies empowers schools with a suite of solutions designed to increase visibility, improve communication, and empower informed decision-making. Our situational awareness solutions create a proactive safety environment where potential threats can be identified and addressed swiftly, with clear communication protocols that are vital for creating a truly secure learning environment.
Forensic Investigation
Preserving Evidence, Aiding Investigations: Forensic Investigation for Schools
When security incidents occur, preserving evidence is critical. ICU Technologies can connect your campus security systems with professional forensic investigation protocols, ensuring valuable evidence is captured, protected, and readily available for law enforcement. Our video management systems with forensic investigation capabilities allow for detailed review of security footage, helping law enforcement in piecing together the timeline of any event.
Teacher and Staff Security
Empowering Educators: Teacher & Staff Security Solutions
Educators are the heart of the school community. ICU Technologies recognizes the importance of their safety and well-being. We offer a range of personal security solutions designed to empower teachers and staff to focus on their students, while feeling safe and secure, including personal duress and panic alert buttons that can be worn around the neck and activated at any time.

Case Study Spotlight
Bridging Communication Gaps
ICU Technologies Fosters Collaboration for Enhanced Security at Stockton Unified School District
- Connecting with stakeholders in various departments
- Opening lines of communication between departments
- Highlighting areas of opportunity to enhance student safety
Stockton Unified School District aimed to bolster their security posture, but lacked a clear understanding of individual departmental needs. ICU Technologies took a unique approach, bringing together staff across various departments to identify critical security gaps and communication silos. By facilitating open communication and aligning departmental goals, ICU helped Stockton Unified pinpoint previously unseen vulnerabilities. This collaborative process led to the development of a comprehensive security plan that addressed these vulnerabilities and fostered a more unified approach to school safety across the district.
More Case StudiesBuild a Safer Campus. Contact ICU Technologies
Learn More About Our Proven Process
We understand that school districts want partners, not vendors. Connect with our K-12 security specialists today to explore how our Proven Process can help your district identify and unite stakeholders to achieve your security objectives.
CALL US: (530) 488.7200
Contact Our Team